|
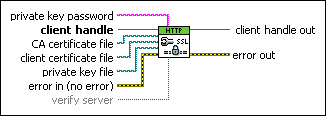
private key password specifies a password for the private key file. If the private key file is not encrypted, you do not have to specify a private key password.
|
 |
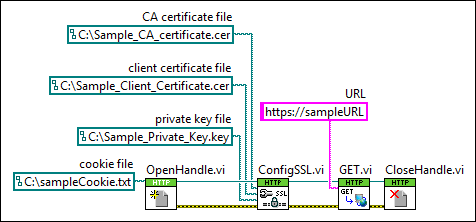
client handle specifies the client handle to associate with the Web request. Use client handles to wire together multiple HTTP Client VIs while preserving authentication credentials, HTTP headers, and cookies. Client handles are not required when making independent Web requests without persistent data such as headers or credentials.
|
 |
CA certificate file specifies the path to a list of trusted certificate authority (CA) certificates. If you specify TRUE for the verify server control, the client verifies the server's identity against this list of trusted certificates.
|
 |
private key file specifies the path to a private key file that is part of the client certificate and client authentication process. If the server requires client authentication, you must specify a client certificate file and a private key file. If you need to transfer this file between client systems, especially over a network, you can assign a password when you create the private key file. To use password-protected private key files with this VI, assign the password to the private key password input.
|
 |
error in describes error conditions that occur before this node runs. This input provides standard error in functionality.
|
 |
verify server specifies whether to check the server's certificate against the list of trusted CA certificates specified by the CA certificate file control. If TRUE, this VI verifies the server's identity against the list of trusted CA certificates for optimal security. If FALSE, this VI does not verify the server's identity and does not provide optimal security. Specifying FALSE allows the client to accept self-signed certificates signed by the certificate creator rather than a trusted CA. The default is TRUE.
|
 |
client handle out returns the client handle associated with the Web request. Use client handles to wire together multiple HTTP Client VIs while preserving authentication credentials, HTTP headers, and cookies. Client handles are not required when making independent Web requests without persistent data such as headers or credentials.
|
 |
error out contains error information. This output provides standard error out functionality.
|
Use the ConfigSSL VI to verify the server's identity against a list of trusted certificate authority (CA) certificates, and provide client authentication, if required by the server. Client handles save the TLS/SSL credentials across multiple Web requests. Use the OpenHandle VI to open a client handle.
TLS/SSL encryption uses certificates to establish secure connections between a client and a server. Certificates are binary files that contain identifying information about the server, as well as a public key and a digital signature. The digital signature can be added by a certificate authority (CA), a trusted third party that issues digital certifications, or by the certificate creator, which is called a self-signed certificate.
 Add to the block diagram
Add to the block diagram Find on the palette
Find on the palette